Contributed by Dan Lorenc | originally posted on medium.com
This post accompanies a talk I just gave at the 2021 Open Source Summit, called Zero Trust Supply Chain Security. The slides are available here.
Background
Let’s say you’re walking down the sidewalk outside of your office, and you find a USB thumb drive sitting on the ground. I hope everyone knows that you should absolutely not take that drive inside your office and plug it into your workstation. Everyone in software should (rightly) be screaming no right now! Real attacks have happened this way, and security orgs across the world hammer this into all employees as part of training.
But for some reason, we don’t even pause to think twice before running docker pull or npm install, even though these are arguably worse than plugging in a random USB stick! Both situations involve taking code from someone you do not trust and running it, but the docker container or NPM package will eventually make it all the way into your production environment!
Zero Trust
Traditionally, network and workload security relied on trusted “perimeters”. Firewalls, internal networks and physical security provided defense against attackers by keeping them out. This type of architecture is simple and effective when all assets are in one place, the firewall doesn’t need many holes and all hardware is on the same physical network.
Unfortunately, this isn’t true anymore. The workplace is distributed. Devices are mobile and environments are ephemeral. Enter zero-trust security. Zero-trust architecture focuses on protecting assets, not perimeters. Services authenticate users against hardware instead of network endpoints. Users authenticate with multi-factor-authentication (FIDO2, etc.) and devices authenticate with hardware-roots-of-trust (TPM2, etc.). The end result is a system focused on fine-grained access control. Instead of trusting every device on a network, you control exactly which users and systems have access to which services.
In a supply chain, artifacts travel along a series of repositories (source code or binary artifact) as they are transformed from initial commit to running artifact in a production environment and trust is typically managed at the repository-level. An organization trusts an SCM for their first-party code, and a series of artifact managers (language, container) for their third-party code. Stricter companies may require all artifacts to be mirrored into a fully-trusted first-party repository. In these scenarios, trust moves internal but remains at the repository level.
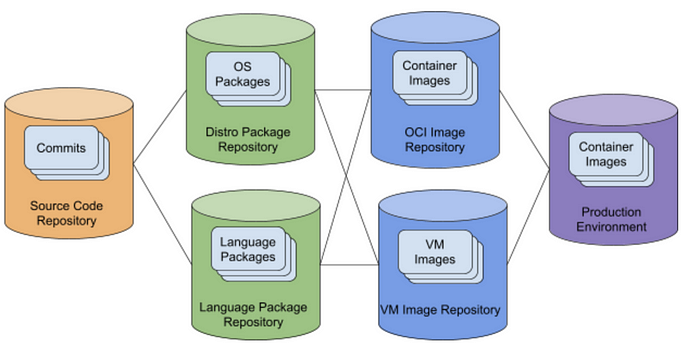
In typical open source supply-chains, a compromise in any one of these systems is enough to attack the final system. There are typically many more separate systems than depicted above, and many are run for free by open-source communities with low or zero budgets.
A Zero Trust Supply Chain moves artifact repositories out of the Trusted Compute Base. Individuals and build systems attest to source code and artifacts directly. These attestations form a verifiable chain from its origin (developer or system) to final, deployed production artifact. Artifact metadata (including rich provenance) is digitally-signed with PKI support. Signed metadata files, or attestations, are stored and accessible in a global transparency log.

Instead of trusting the systems to serve accurate package metadata, we verify each claim in the chain itself against the actors or systems that attested to them.
The Challenge With Zero Trust Supply Chain Security
Supply-chain security is very similar to network security and identity management. Instead of authenticating people or systems, we need to authenticate artifacts. There are multiple systems in use today, but all rely on cryptographic signatures and some form of PKI.
Existing PKI systems for artifact signing include distributed systems like PGP’s Web of Trust or TOFU models, centralized systems like Apple and the Play Store’s code-signing systems, as well as hierarchical CA systems like Authenticode. Newer technologies like transparency logs are also starting to serve a role, with usage in the Go modules ecosystem as well other Binary transparency implementations.
Authenticating an artifact is similar to authenticating a system or an individual in many ways, but it also differs in a few key ways that mean the existing technologies don’t map perfectly. The biggest difference is that artifacts are not “alive”. An artifact is like a rock. It cannot vouch for, or attest to its own identity like a person or system can. A person can vouch for their own identity by entering a password, touching a token or even meeting in person to show a government ID. A system can vouch for its identity by responding to a challenge (like in ACME) or using a hardware root-of-trust with something like a TPM. If you ask an artifact who it is, it just sits there like a rock.
This might sound silly, but has large implications on the way we need to design authentication systems. Cryptographic authentication systems usually rely on one party possessing a secret, and using this secret to complete challenges that prove they still have possession of this secret. If this secret is lost or stolen, the protocol fails and the user must recover their identity in some way. Well-designed systems acknowledge that secrets cannot be kept secret forever, so they include some form of automatic rotation or expiration.
This means users or systems must periodically obtain or generate new secrets to use to attest to their identity. Each protocol specifies exactly how this works (ACME for Web PKI, cookie, session or JWT expiration for user logins, etc.), but the key problem is that they require some active form of interaction from the user/system. Artifacts are just rocks sitting on the ground, so they can’t do this.
Getting Started
The problem statement was simple — why can’t you run a random binary package or container that you find on the sidewalk? Why is there no way to determine where any given container came from? Basic questions, like who built it, from what source, and how? Some great projects like In-Toto and The Update Framework have been working on this problem for years, but they were still missing a few parts that we set out to solve in Sigstore.
These missing parts were:
- an easy to use signing system
- a central discovery and storage system for build attestations
- automatic build system integrations.
Through Sigstore, TektonCD, SPIFFE/SPIRE and a few other projects, we’ve solved these missing pieces. This post shows how to put them together into one cohesive system, and how an end user can trace an artifact from a production cluster all the way back to the code that went into it.
The Pieces
Sigstore makes signing of arbitrary artifacts dead simple with the cosigntool, including built-in support for cloud KMS systems, physical HSMs, yubikey devices, and Sigstore’s free code-signing CA based on Open ID Connect.
Sigstore also provides a central binary transparency log called Rekor, based on the same technology that powers Certificate Transparency in almost every major browser today. Rekor can act as an immutable, verifiable ledger containing metadata about software artifacts that can be looked up by anyone given only an artifact hash.
On top of Rekor, we’ve also built an Attestation Transparency system, allowing for the storage and retrieval of rich In-Toto attestations that contain the full build history of any given artifact, including the exact tools, source code and build system that was used.
Finally, we’ve started to integrate all of these parts together into build systems, so it all happens automatically. TektonCD was designed with supply-chain security in mind from day one, and the Tekton Chains project has been a perfect place to experiment and add these features!
Enough words, let’s see it in action!
Tracing a Container
For this experiment, we’re going to trace an application container all the way back to the lowest level base image (FROM SCRATCH). We’ll verify signatures and attestations about every step in this build process, across multiple build systems run by different organizations!
You can follow along from your own machine by installing the crane, cosign, and rekor-cli tools, or see the commands here. The overall build process looks like this:
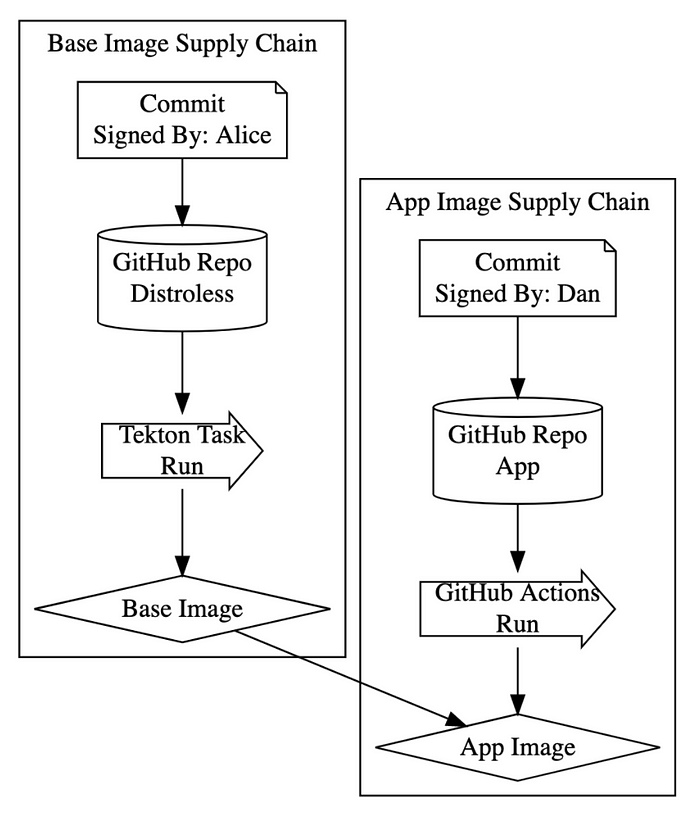
Step 1: The Application Container
The demo starts with a container image built using the ko build tool inside of a GitHub Action. We’ll verify the signatures on this application image, which are signed using an ambient token made available by the GitHub Actions platform. This token is bound to a specific invocation of the action at a specific commit, which we can lookup in the transparency log.
The container image is built from the github.com/dlorenc/hello-ko repository, and is available at ghcr.io/dlorenc/hello-ko.
We’ll start by looking up signatures for that image:
| % COSIGN_EXPERIMENTAL=1 cosign verify ghcr.io/dlorenc/hello-ko | jq . | |
| Verification for ghcr.io/dlorenc/hello-ko:latest -- | |
| The following checks were performed on each of these signatures: | |
| - The cosign claims were validated | |
| - Existence of the claims in the transparency log was verified offline | |
| - Any certificates were verified against the Fulcio roots. | |
| [ | |
| { | |
| "critical": { | |
| "identity": { | |
| "docker-reference": "ghcr.io/dlorenc/hello-ko" | |
| }, | |
| "image": { | |
| "docker-manifest-digest": "sha256:d4e7259f37b477bf9b6539459c2cbf2611fcdb7233dbf8b76c971d9df01a368f" | |
| }, | |
| "type": "cosign container image signature" | |
| }, | |
| "optional": { | |
| "Bundle": { | |
| "SignedEntryTimestamp": "MEUCIQDy8KU/306TmyZla0Uxvq9ap6BG9WBBZNVWkqZcT1iI3wIgDZQ969rVT9XjUUGjDbGRjDMnTaub/bVN37UIuGIItR0=", | |
| "Payload": { | |
| "body": "eyJhcGlWZXJzaW9uIjoiMC4wLjEiLCJzcGVjIjp7ImRhdGEiOnsiaGFzaCI6eyJhbGdvcml0aG0iOiJzaGEyNTYiLCJ2YWx1ZSI6IjA3ZGVmYTI1ZDYxOTc0MmY1MmU3ZjM0OGU3Y2UxYmQ4YWJlNzgyODljMTBlZDhlZmI0NjVjNTdmYWJiNWNhNDMifX0sInNpZ25hdHVyZSI6eyJjb250ZW50IjoiTUVRQ0lDemlrd2hNbTZabjFhT0piT2Nqc1JUM25xeS82UHVmcE1IWmxkeXFXSXVWQWlBZ1dSUXRMS0lpQ2xDRWc3aXNwczBHbXlGK3duUENPZE5kVVBOYklVS3RmUT09IiwiZm9ybWF0IjoieDUwOSIsInB1YmxpY0tleSI6eyJjb250ZW50IjoiTFMwdExTMUNSVWRKVGlCRFJWSlVTVVpKUTBGVVJTMHRMUzB0Q2sxSlNVTjBWRU5EUVdwMVowRjNTVUpCWjBsVlFVeHpNRWhxYkZwWFlVNXViRTl0WlZVeFdHaGtNbWxEWldOcmQwTm5XVWxMYjFwSmVtb3dSVUYzVFhjS1MycEZWazFDVFVkQk1WVkZRMmhOVFdNeWJHNWpNMUoyWTIxVmRWcEhWakpOVWtWM1JIZFpSRlpSVVVSRmQyaDZZVmRrZW1SSE9YbGFWRUZsUm5jd2VRcE5WRUUxVFZScmVVMUVWWGhOZWxKaFJuY3dlVTFVUVRWTlZHdDVUVlJGZUUxNlRtRk5RVUYzVjFSQlZFSm5ZM0ZvYTJwUFVGRkpRa0puWjNGb2EycFBDbEJSVFVKQ2QwNURRVUZTYURWbE1YUlBXakpNVVhoQlVqRlRhMFZzVFV4cVJHRnhNRzVPTTBFMFV5dHhjVk5oUzNONFpFSjVlWEV4YmxOb2VWWjFkbUVLYkZoMGRYUkpRbFZZVXpCRmEwZzRRVGRxTm1oWmEwNXRVRUZuT1c0elZDdHZORWxDV25wRFEwRlhUWGRFWjFsRVZsSXdVRUZSU0M5Q1FWRkVRV2RsUVFwTlFrMUhRVEZWWkVwUlVVMU5RVzlIUTBOelIwRlJWVVpDZDAxRVRVRjNSMEV4VldSRmQwVkNMM2RSUTAxQlFYZElVVmxFVmxJd1QwSkNXVVZHUjNaQkNrVXhjVkV3TkVOdmMzWjRSVlJqUzB0dkwzVk5lREprY1UxQ09FZEJNVlZrU1hkUldVMUNZVUZHVFdwR1NGRkNRbTFwVVhCTmJFVnJObmN5ZFZOMU1Vc0tRblJRYzAxSlIwNUNaMmR5UW1kRlJrSlJZMEpCVVZOQ1owUkNLMDFJZDBkRFEzTkhRVkZWUmtKNlFVTm9ia0p2WkVoU2QwOXBPSFpqU0Vwd1pHMUdNQXBhVjA1b1RGZE9kbUp1VW14aWJsRjBUbXBCZWxwdFZUTmFWR04wVFVSQmQwMURNSGxOYWtrelRGZEtiVTU2VlhSYWFsSnRUbGRWTkUxSFVYbFBWRlV3Q2t4dVRqQmlNMHBvV2pKVmRWb3lPWFphTW5oc1dWaENjR041TldwaU1qQjJXVEpGZWs1dFJYaGFWR3N5VFdwUmVWbHFiRzFaTWtsNFRrUlpkbGt5UlhVS1dUTktNRTFHTkVkQk1WVmtSVkZGUWk5M1VsVk5Sa3RIVlVkb01HUklRbnBQYVRoMldqSnNNR0ZJVm1sTWJVNTJZbE01YTJKSE9YbGFWelZxVERKb2JBcGlSM2gyVEZkMGRreDVOVzVoV0ZKdlpGZEpkbVF5T1hsaE1scHpZak5rZWt3eVNqRmhWM2hyVEc1c2FHSlhlRUZqYlZadFkzazViMXBYUm10amVUbDBDbGxYYkhWTlFXOUhRME54UjFOTk5EbENRVTFFUVRKblFVMUhWVU5OVVVNMVlucGtXRlp4V1ZGM1pVWndhRlV6YkM5VFpYWklURXBOVDBwbWNXNUVNbVlLVXpodlJGQlZMMnd3TVdkNVQyaFhaV1VyVG5GWFFVUjJSMFJ5V0VaaVNVTk5Rak4wYmxsMVlsUkxRbGd6ZWpoQ1lrSmFiM0pUUWtORlV6WkxURXRJUWdwWFRtaFZTMUIyTW01WlEyOU9jVkp0ZEVnMlJWQnJiMVJHVlZGMU1YZERRVWgzUFQwS0xTMHRMUzFGVGtRZ1EwVlNWRWxHU1VOQlZFVXRMUzB0TFFvPSJ9fX0sImtpbmQiOiJyZWtvcmQifQ==", | |
| "integratedTime": 1632084695, | |
| "logIndex": 697473, | |
| "logID": "c0d23d6ad406973f9559f3ba2d1ca01f84147d8ffc5b8445c224f98b9591801d" | |
| } | |
| }, | |
| "Subject": "https://github.com/dlorenc/hello-ko/.github/workflows/build.yaml@refs/heads/main" | |
| } | |
| }, | |
| { | |
| "critical": { | |
| "identity": { | |
| "docker-reference": "ghcr.io/dlorenc/hello-ko" | |
| }, | |
| "image": { | |
| "docker-manifest-digest": "sha256:d4e7259f37b477bf9b6539459c2cbf2611fcdb7233dbf8b76c971d9df01a368f" | |
| }, | |
| "type": "cosign container image signature" | |
| }, | |
| "optional": { | |
| "Bundle": { | |
| "SignedEntryTimestamp": "MEQCIFiwRqIR5iWcVjkLnn8JHH1QFRDBEa5jAJRaIRbsxqkyAiBq+XGrxoX6ontyG02q/hKLhgl3RrYoc+1cIOOHDOymqg==", | |
| "Payload": { | |
| "body": "eyJhcGlWZXJzaW9uIjoiMC4wLjEiLCJzcGVjIjp7ImRhdGEiOnsiaGFzaCI6eyJhbGdvcml0aG0iOiJzaGEyNTYiLCJ2YWx1ZSI6IjU1YzQ4ZTFlNTQyZjg0OTQ2YjZlNzU3ZmVkOWIzZGEyNGM5ZjBkZGE3MTE4ZTA1ZGEzZTAxNGRlODQ3YzRlOGMifX0sInNpZ25hdHVyZSI6eyJjb250ZW50IjoiTUVZQ0lRQ0dRTWFaNmVDS1Z3QXVWUHo4bFFMaVhlQXY2aTJMY0grWnJweC9RU2xBTVFJaEFJVjZhL295ZnhrejJTT2JZMGU2L1ErL0FQVDRtWXBHcXpaRGhRdmUrcUU4IiwiZm9ybWF0IjoieDUwOSIsInB1YmxpY0tleSI6eyJjb250ZW50IjoiTFMwdExTMUNSVWRKVGlCRFJWSlVTVVpKUTBGVVJTMHRMUzB0Q2sxSlNVTjBWRU5EUVdwMVowRjNTVUpCWjBsVlFWQnJXR3g0ZHk5VlpqYzBOVGxCY1hVMFdFNDRiamhoZUVZMGQwTm5XVWxMYjFwSmVtb3dSVUYzVFhjS1MycEZWazFDVFVkQk1WVkZRMmhOVFdNeWJHNWpNMUoyWTIxVmRWcEhWakpOVWtWM1JIZFpSRlpSVVVSRmQyaDZZVmRrZW1SSE9YbGFWRUZsUm5jd2VRcE5WRUUxVFdwQmQwMVVVWGROZW1SaFJuY3dlVTFVUVRWTmFrRjNUV3BCZDAxNldtRk5RVUYzVjFSQlZFSm5ZM0ZvYTJwUFVGRkpRa0puWjNGb2EycFBDbEJSVFVKQ2QwNURRVUZUUkVaNmRXTk5lWEZ0UlRWblJVZHFhbmxwYzBGb1VWSk5jVGc0WmxkRVlVSnRiM1pIUzA1dlR6TjBjMnc1ZFZKaU5GUmlOVGtLTlVjNVJXcEZaRGh0VjNoS2R5dFFaRFpuWldZNFdXczVXRVJsUkZRd01tOXZORWxDV25wRFEwRlhUWGRFWjFsRVZsSXdVRUZSU0M5Q1FWRkVRV2RsUVFwTlFrMUhRVEZWWkVwUlVVMU5RVzlIUTBOelIwRlJWVVpDZDAxRVRVRjNSMEV4VldSRmQwVkNMM2RSUTAxQlFYZElVVmxFVmxJd1QwSkNXVVZHUWxaNUNrUlBhMmwwWTBGRlprdHdibTgwZVdkNk5HZFFTRTU0Y2sxQ09FZEJNVlZrU1hkUldVMUNZVUZHVFdwR1NGRkNRbTFwVVhCTmJFVnJObmN5ZFZOMU1Vc0tRblJRYzAxSlIwNUNaMmR5UW1kRlJrSlJZMEpCVVZOQ1owUkNLMDFJZDBkRFEzTkhRVkZWUmtKNlFVTm9ia0p2WkVoU2QwOXBPSFpqU0Vwd1pHMUdNQXBhVjA1b1RGZE9kbUp1VW14aWJsRjBUbXBCZWxwdFZUTmFWR04wVFVSQmQwMURNSGxOYWtrelRGZEtiVTU2VlhSYWFsSnRUbGRWTkUxSFVYbFBWRlV3Q2t4dVRqQmlNMHBvV2pKVmRWb3lPWFphTW5oc1dWaENjR041TldwaU1qQjJXVEpGZWs1dFJYaGFWR3N5VFdwUmVWbHFiRzFaTWtsNFRrUlpkbGt5UlhVS1dUTktNRTFHTkVkQk1WVmtSVkZGUWk5M1VsVk5Sa3RIVlVkb01HUklRbnBQYVRoMldqSnNNR0ZJVm1sTWJVNTJZbE01YTJKSE9YbGFWelZxVERKb2JBcGlSM2gyVEZkMGRreDVOVzVoV0ZKdlpGZEpkbVF5T1hsaE1scHpZak5rZWt3eVNqRmhWM2hyVEc1c2FHSlhlRUZqYlZadFkzazViMXBYUm10amVUbDBDbGxYYkhWTlFXOUhRME54UjFOTk5EbENRVTFFUVRKblFVMUhWVU5OUW1OQlZqSjNSV2t5ZEdKRldtRnVXUzk1TVVkSU16ZFdaMHBVWTJkbGEyaHVSbEFLZEVjMU9HSlhkemR5WjBKM016UnpjRzgwU0RWWWVXaG1Wamt4UmxOM1NYaEJUa1IyY1hoTmJGRklUa2c1U1d0RmRFNXNSMlZuV1U1RFJVZHplVTVKZUFwUk1IZDFNRUpEYTJObmJVUkNRak5pZVdSVVFtbHdaRk5ZZUhoeVIzYzJlVWhSUFQwS0xTMHRMUzFGVGtRZ1EwVlNWRWxHU1VOQlZFVXRMUzB0TFFvPSJ9fX0sImtpbmQiOiJyZWtvcmQifQ==", | |
| "integratedTime": 1632102037, | |
| "logIndex": 697503, | |
| "logID": "c0d23d6ad406973f9559f3ba2d1ca01f84147d8ffc5b8445c224f98b9591801d" | |
| } | |
| }, | |
| "Subject": "https://github.com/dlorenc/hello-ko/.github/workflows/build.yaml@refs/heads/main", | |
| "git_sha": "e0449b31dfa7794964fcf2370392f269962c4488" | |
| } | |
| } | |
| ] |
Here we can see that there is a valid signature for the image! The image was signed by an ephemeral certificate issued by the Fulcio CA, and bound to a specific GitHub Action. We can see this action in theSubject field of the certificate, and here it has been set to https://github.com/dlorenc/hello-ko/.github/workflows/build.yaml@refs/heads/main. The specific git commit the container was built at is also contained in the payload: git_sha”: “e0449b31dfa7794964fcf2370392f269962c4488.
Let’s pause briefly for effect: we’ve now looked up and cryptographically verified the exact build and commit a container image was built from! That’s pretty cool.
But that’s not all! We can check the source as well. Supply chain security is so tough to get right because there are so many different attack points in even a simple release process. The SLSA project contains a great overview and breakdown of these points, you can see them in a map here:

For this case, we’ve verified the commit something happened at, but we still don’t know if that commit should be trusted. The source code repository itself could have been compromised, or someone might have obtained permissions by accident. To solve this, we can check for commit signatures!
We’ll do this again using Rekor, by looking for signatures in the transparency log. After a bit of jq magic, we get the email address that the commit was signed by in the Subject field, my own personal one: email:lorenc.d@gmail.com
| % rekor-cli search --artifact <(echo -n e0449b31dfa7794964fcf2370392f269962c4488) | |
| Found matching entries (listed by UUID): | |
| 989e11cf2a390596821f879556d62d5b86e1022fd9f82bc2db37d0b121c46b3c | |
| % rekor-cli get --uuid 989e11cf2a390596821f879556d62d5b86e1022fd9f82bc2db37d0b121c46b3c --format=json | jq -r .Body.RekordObj.signature.publicKey.content | base64 -D | openssl x509 -text -noout | |
| Certificate: | |
| Data: | |
| Version: 3 (0x2) | |
| Serial Number: | |
| 3a:a8:18:85:65:22:3a:cf:9b:ed:f1:af:14:bd:08:eb:d9:23:2d | |
| Signature Algorithm: ecdsa-with-SHA384 | |
| Issuer: O=sigstore.dev, CN=sigstore | |
| Validity | |
| Not Before: Sep 20 01:41:52 2021 GMT | |
| Not After : Sep 20 02:01:51 2021 GMT | |
| Subject: | |
| Subject Public Key Info: | |
| Public Key Algorithm: id-ecPublicKey | |
| Public-Key: (256 bit) | |
| pub: | |
| 04:d7:1c:01:8f:5e:7c:f0:b8:c9:aa:6a:80:67:48: | |
| 6f:ff:f1:f9:15:80:03:66:68:fc:62:8c:b7:16:c1: | |
| 36:60:96:de:69:f4:14:ed:0c:8c:ff:f0:f8:2a:23: | |
| 3b:d5:ba:f5:83:05:87:e5:28:7f:d1:2c:2a:1d:62: | |
| 53:60:2c:07:fd | |
| ASN1 OID: prime256v1 | |
| NIST CURVE: P-256 | |
| X509v3 extensions: | |
| X509v3 Key Usage: critical | |
| Digital Signature | |
| X509v3 Extended Key Usage: | |
| Code Signing | |
| X509v3 Basic Constraints: critical | |
| CA:FALSE | |
| X509v3 Subject Key Identifier: | |
| 1F:C3:20:F2:1E:FC:88:ED:50:B3:98:3D:F0:00:1B:8A:32:C2:A1:54 | |
| X509v3 Authority Key Identifier: | |
| keyid:C8:C5:1D:00:41:9A:24:29:32:51:24:EB:0D:AE:4A:ED:4A:06:D3:EC | |
| Authority Information Access: | |
| CA Issuers - URI:http://privateca-content-603fe7e7-0000-2227-bf75-f4f5e80d2954.storage.googleapis.com/ca36a1e96242b9fcb146/ca.crt | |
| X509v3 Subject Alternative Name: critical | |
| email:lorenc.d@gmail.com | |
| Signature Algorithm: ecdsa-with-SHA384 | |
| 30:64:02:30:28:bb:e5:38:fb:74:09:86:c6:6c:e9:d5:23:93: | |
| ee:64:c0:19:fc:43:90:7a:3a:f2:eb:76:22:ca:c2:5a:8c:d8: | |
| 8d:ee:c3:ad:b2:07:2a:0d:8b:51:66:c7:9c:a6:0f:17:02:30: | |
| 69:e4:85:9e:4f:19:45:3c:d2:52:89:ee:b1:a8:d3:9d:6a:4a: | |
| a7:a8:d9:d6:a1:31:7e:19:98:69:6c:55:ba:45:12:6f:4a:58: | |
| a9:72:4f:b2:27:00:c7:50:d5:bc:26:97 |
Step 2: The Base Image
So now we’ve verified the application image and the commit used to build it. We can keep going though, and look for more turtles on the way down. Most containers are built from a base image, which can also be attacked! Thanks to a recent change in the OCI, image build tools can include an annotation that points to the specific base image and digest used during a build.
We’ll lookup that annotation using crane, and find that it’s gcr,io/distroless/static:nonroot, at digest sha256:c070202f5ea785303a9f8cfc5f094d210336e3e0ef09806b2edcce3d5e223eb7:
| % crane manifest ghcr.io/dlorenc/hello-ko | jq . | |
| { | |
| "schemaVersion": 2, | |
| "mediaType": "application/vnd.docker.distribution.manifest.v2+json", | |
| "config": { | |
| "mediaType": "application/vnd.docker.container.image.v1+json", | |
| "size": 1030, | |
| "digest": "sha256:3c66e55e00382386785c04a95fdb9c04b67c3f1505e447410a66b2573ca00e65" | |
| }, | |
| "layers": [ | |
| { | |
| "mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip", | |
| "size": 657696, | |
| "digest": "sha256:b49b96595fd4bd6de7cb7253fe5e89d242d0eb4f993b2b8280c0581c3a62ddc2" | |
| }, | |
| { | |
| "mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip", | |
| "size": 127, | |
| "digest": "sha256:250c06f7c38e52dc77e5c7586c3e40280dc7ff9bb9007c396e06d96736cf8542" | |
| }, | |
| { | |
| "mediaType": "application/vnd.docker.image.rootfs.diff.tar.gzip", | |
| "size": 1081108, | |
| "digest": "sha256:84e71c49ff5a9ca83fdfbb8828333efde9818970377a872b28ea6d40cb61d691" | |
| } | |
| ], | |
| "annotations": { | |
| "org.opencontainers.image.base.digest": "sha256:c070202f5ea785303a9f8cfc5f094d210336e3e0ef09806b2edcce3d5e223eb7", | |
| "org.opencontainers.image.base.name": "gcr.io/distroless/static:nonroot" | |
| } | |
| } |
Then, we look for signatures. We find one valid signature with a Subject of keyless@distroless.iam.gserviceaccount.com , which is the correct service account used to sign these images in the repository.
| % cosign verify gcr.io/distroless/static:nonroot | jq . | |
| Verification for gcr.io/distroless/static:nonroot -- | |
| The following checks were performed on each of these signatures: | |
| - The cosign claims were validated | |
| - Existence of the claims in the transparency log was verified offline | |
| - Any certificates were verified against the Fulcio roots. | |
| [ | |
| { | |
| "critical": { | |
| "identity": { | |
| "docker-reference": "gcr.io/distroless/static" | |
| }, | |
| "image": { | |
| "docker-manifest-digest": "sha256:07869abb445859465749913267a8c7b3b02dc4236fbc896e29ae859e4b360851" | |
| }, | |
| "type": "cosign container image signature" | |
| }, | |
| "optional": { | |
| "Bundle": { | |
| "SignedEntryTimestamp": "MEUCIQDOn8SsMNq0G1kiXAByZbrWKMPuHFfJQbgzlUfMSsU/FwIgRWUUCUFKCpDth3lf/MWpoMTCsNf+A19ilqWvck0YDJ8=", | |
| "Payload": { | |
| "body": "eyJhcGlWZXJzaW9uIjoiMC4wLjEiLCJzcGVjIjp7ImRhdGEiOnsiaGFzaCI6eyJhbGdvcml0aG0iOiJzaGEyNTYiLCJ2YWx1ZSI6ImFkMGNlMWE1NDczMGQ1ZmM0YWQzYmIzOGMwZDEwYTk4NzBiMDQ3M2I4YjgxYWQyNmM2NzA3ZGRmOTMxNTk4MTkifX0sInNpZ25hdHVyZSI6eyJjb250ZW50IjoiTUVRQ0lFbVZPTmtSUVJsdndWb1hTR3YzZDYwMVdDRzg1YlJXWDBZQTEwQURyelJwQWlBdWNsZ3liZFpnVk5HdEhIRGQxZEJuendFdStTVTRRNDY0WmJmT1lxN3hpQT09IiwiZm9ybWF0IjoieDUwOSIsInB1YmxpY0tleSI6eyJjb250ZW50IjoiTFMwdExTMUNSVWRKVGlCRFJWSlVTVVpKUTBGVVJTMHRMUzB0Q2sxSlNVTnJSRU5EUVdoWFowRjNTVUpCWjBsVlFVa3pVSGR6T0dwalozVmFlRmxYZURaeldUVnBObkU0VGswd2QwTm5XVWxMYjFwSmVtb3dSVUYzVFhjS1MycEZWazFDVFVkQk1WVkZRMmhOVFdNeWJHNWpNMUoyWTIxVmRWcEhWakpOVWtWM1JIZFpSRlpSVVVSRmQyaDZZVmRrZW1SSE9YbGFWRUZsUm5jd2VRcE5WRUUxVFdwcmVFNXFSVE5PUkZKaFJuY3dlVTFVUVRWTmFtdDRUbXBOTTA1RVRtRk5RVUYzVjFSQlZFSm5ZM0ZvYTJwUFVGRkpRa0puWjNGb2EycFBDbEJSVFVKQ2QwNURRVUZUYm1JME9WbHdjVmR1Ym10WE9YZE5jalV6TjIxbGVrbDFlVTVvTldzNGREUmtWREozZUZGUGQxRkpORW8zVVhVeVFVRnFSRThLVTJkdlNta3dka2hyZVU5aloyaHhSa0pVVEhWS2JXUmtLMVF6UzB4TksxUnZORWxDVVZSRFEwRlVNSGRFWjFsRVZsSXdVRUZSU0M5Q1FWRkVRV2RsUVFwTlFrMUhRVEZWWkVwUlVVMU5RVzlIUTBOelIwRlJWVVpDZDAxRVRVRjNSMEV4VldSRmQwVkNMM2RSUTAxQlFYZElVVmxFVmxJd1QwSkNXVVZHU3pJdkNtWlpZVTUxWlRGalNHeGlVa2hzZVVSdWIyVnNWMEpITTAxQ09FZEJNVlZrU1hkUldVMUNZVUZHVFdwR1NGRkNRbTFwVVhCTmJFVnJObmN5ZFZOMU1Vc0tRblJRYzAxSlIwNUNaMmR5UW1kRlJrSlJZMEpCVVZOQ1owUkNLMDFJZDBkRFEzTkhRVkZWUmtKNlFVTm9ia0p2WkVoU2QwOXBPSFpqU0Vwd1pHMUdNQXBhVjA1b1RGZE9kbUp1VW14aWJsRjBUbXBCZWxwdFZUTmFWR04wVFVSQmQwMURNSGxOYWtrelRGZEtiVTU2VlhSYWFsSnRUbGRWTkUxSFVYbFBWRlV3Q2t4dVRqQmlNMHBvV2pKVmRWb3lPWFphTW5oc1dWaENjR041TldwaU1qQjJXVEpGZWs1dFJYaGFWR3N5VFdwUmVWbHFiRzFaTWtsNFRrUlpkbGt5UlhVS1dUTktNRTFFWjBkQk1WVmtSVkZGUWk5M1VYVk5RM2xDUzIxMGJHVlhlR3hqTTA1QldrZHNlbVJJU25aaVIxWjZZM2sxY0ZsWE1IVmFNMDVzWTI1YWNBcFpNbFpvV1RKT2RtUlhOVEJNYlU1MllsUkJTMEpuWjNGb2EycFBVRkZSUkVGM1RuQkJSRUp0UVdwRlFYUXZha2RVVVRadlRGVndOekpaTjJwRWMxWllDbGh2YmxwRlFtNVNSM3BUY1ZGWFMyRjZXREYyV2s0eU9ERkNPRGMxVEhKU2EzTlNLMHRZWm5vMFFrODVRV3BGUVRBd1lUQlBZakJWYTBkSlJHaEhPVUVLU0ZKak56QTRZWEJxVkdodlJtUk1NRzlvY21KWUsxTXhRVTFrWjJ4eFVXUkZhRTB5UkdFM1RtSXZNMWxVV1ZKbUNpMHRMUzB0UlU1RUlFTkZVbFJKUmtsRFFWUkZMUzB0TFMwSyJ9fX0sImtpbmQiOiJyZWtvcmQifQ==", | |
| "integratedTime": 1632932265, | |
| "logIndex": 723949, | |
| "logID": "c0d23d6ad406973f9559f3ba2d1ca01f84147d8ffc5b8445c224f98b9591801d" | |
| } | |
| }, | |
| "Subject": "keyless@distroless.iam.gserviceaccount.com" | |
| } | |
| } | |
| ] |
We can go a bit further here though, because the distroless images are reproducible. These images are actually built in multiple build systems to compare their hashes. One of the build systems used here is TektonCD, configured with Tekton Chains to produce In-Toto Provenance Attestations. The overall system architecture was described by Priya Wadhwa in this great blog post.
To lookup this provenance, we’ll start with the base image digest from above and search for entries in the transparency log. After some unpacking, we can find the full Tekton Provenance for the build.
| % rekor-cli search --sha sha256:c070202f5ea785303a9f8cfc5f094d210336e3e0ef09806b2edcce3d5e223eb7 | |
| Found matching entries (listed by UUID): | |
| 1b4525da91420266a4d5f41e7191bdceeb26d2fc99681c45536b6e79cf55ceb7 | |
| % rekor-cli get --uuid 1b4525da91420266a4d5f41e7191bdceeb26d2fc99681c45536b6e79cf55ceb7 --format=json | jq -r .Attestation | base64 -D | jq -r . | |
| { | |
| "_type": "https://in-toto.io/Statement/v0.1", | |
| "predicateType": "https://tekton.dev/chains/provenance", | |
| "subject": [ | |
| { | |
| "name": "gcr.io/distroless/base", | |
| "digest": { | |
| "sha256": "cc77e329ba773e35e868c56f90b5b049b189ec53edcf0a583827a8d3b5e75e02" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/base-debian10", | |
| "digest": { | |
| "sha256": "cc77e329ba773e35e868c56f90b5b049b189ec53edcf0a583827a8d3b5e75e02" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/base-debian11", | |
| "digest": { | |
| "sha256": "4bf4804b8d8c41c6e5bbdf0be90dfdf8abacbd7652cb317b5689a2c615c8d14b" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/base-debian11", | |
| "digest": { | |
| "sha256": "74e96a2b930b250fb623e5219210625c583ec2b147576f9696340ad13fbf5fc5" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/base-debian11", | |
| "digest": { | |
| "sha256": "76976398fc199af915198766e13a036a9b003be89655491342ddbd0441a96761" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/base-debian11", | |
| "digest": { | |
| "sha256": "45e767df9f6c72363e5a53a01457cc5a7d6e1106fd9c71ab0594be9cb1d25841" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/cc", | |
| "digest": { | |
| "sha256": "e995c19490ce4445c28d85ed03975cdf3a9084dab54e0a865b78417db0aa98af" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/cc", | |
| "digest": { | |
| "sha256": "d49304c8f3a0a08507f6847f4454b30d2d138e00ba518ff2ee3b04144e39f149" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/cc-debian10", | |
| "digest": { | |
| "sha256": "e995c19490ce4445c28d85ed03975cdf3a9084dab54e0a865b78417db0aa98af" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/cc-debian10", | |
| "digest": { | |
| "sha256": "d49304c8f3a0a08507f6847f4454b30d2d138e00ba518ff2ee3b04144e39f149" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/java-debian11", | |
| "digest": { | |
| "sha256": "4e785ae877ae3a432f5d7f3d34c2433de8979909de066c63625dcf352027fdfb" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/java-debian11", | |
| "digest": { | |
| "sha256": "44e8434d8552061858cad9d9a5c4009cc2ed17a586248029796c3a28187d4e31" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/java-debian11", | |
| "digest": { | |
| "sha256": "1b3e05376d83a35baa07b1e9ddea22ae9acadc2c182234ba0459c6543c46a4a3" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/java-debian11/jetty", | |
| "digest": { | |
| "sha256": "8f8c1b563fd734a494d460ef1e7ddafe82e46ba676521ad7e68ac0c3dd67450f" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/java-debian11/jetty", | |
| "digest": { | |
| "sha256": "8f8c1b563fd734a494d460ef1e7ddafe82e46ba676521ad7e68ac0c3dd67450f" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3", | |
| "digest": { | |
| "sha256": "5b1cdc43796ab7d44600a0043e5dc8b70b7eb041dc3f4c65c290e202b793e4d0" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3", | |
| "digest": { | |
| "sha256": "b79dc6841b1d2de48232e8e30c52b9d4408d6f3234e9179d88ef66eb92530e9c" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3-debian10", | |
| "digest": { | |
| "sha256": "b79dc6841b1d2de48232e8e30c52b9d4408d6f3234e9179d88ef66eb92530e9c" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3-debian10", | |
| "digest": { | |
| "sha256": "5b1cdc43796ab7d44600a0043e5dc8b70b7eb041dc3f4c65c290e202b793e4d0" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3-debian11", | |
| "digest": { | |
| "sha256": "dc1cfc7fa1a3c7ba436e58c87c03c21722cd1445848139285576d177de0de76a" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/python3-debian11", | |
| "digest": { | |
| "sha256": "6138876fe0efac0701569aa097bd754f9e8be628da1a03b1839386b654496b23" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static", | |
| "digest": { | |
| "sha256": "8dc6124a1429a5400c2cbfc971b360fd2ab6c495d59f83e3033af8dbc720888b" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static", | |
| "digest": { | |
| "sha256": "c1a8f9c6da688e240fd4b6add7c8240315316b61873dc9ad9d011d08895943c0" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static", | |
| "digest": { | |
| "sha256": "c070202f5ea785303a9f8cfc5f094d210336e3e0ef09806b2edcce3d5e223eb7" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static", | |
| "digest": { | |
| "sha256": "fd36065a1b108a5970856a1b10092fa284635f190dd082651cc70e191184fdae" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static-debian10", | |
| "digest": { | |
| "sha256": "c070202f5ea785303a9f8cfc5f094d210336e3e0ef09806b2edcce3d5e223eb7" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static-debian10", | |
| "digest": { | |
| "sha256": "8dc6124a1429a5400c2cbfc971b360fd2ab6c495d59f83e3033af8dbc720888b" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static-debian10", | |
| "digest": { | |
| "sha256": "fd36065a1b108a5970856a1b10092fa284635f190dd082651cc70e191184fdae" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static-debian10", | |
| "digest": { | |
| "sha256": "c1a8f9c6da688e240fd4b6add7c8240315316b61873dc9ad9d011d08895943c0" | |
| } | |
| }, | |
| { | |
| "name": "gcr.io/distroless/static-debian11", | |
| "digest": { | |
| "sha256": "941f674ca6ad89588eeee59ef57fe107377871285dadd2c660e9f58edb986374" | |
| } | |
| } | |
| ], | |
| "predicate": { | |
| "invocation": { | |
| "parameters": [ | |
| "MANIFEST_SUBSECTION={string 2 []}", | |
| "CHAINS-GIT_COMMIT={string 6cdf24fcc47ec93f370ea591f7ff460641a1ac5c []}", | |
| "CHAINS-GIT_URL={string https://github.com/GoogleContainerTools/distroless []}" | |
| ], | |
| "recipe_uri": "task://distroless-provenance", | |
| "event_id": "f2d81a68-bd2f-4574-ba23-8990259ab85d", | |
| "builder.id": "tekton-chains" | |
| }, | |
| "recipe": { | |
| "steps": [ | |
| { | |
| "entryPoint": "#!/bin/sh\nset -ex\n\n# get the digests for a subset of images built, and store in the IMAGES result\ngo run provenance/provenance.go images $(params.MANIFEST_SUBSECTION) > $(results.IMAGES.path)\n", | |
| "arguments": null, | |
| "environment": { | |
| "container": "provenance", | |
| "image": "docker.io/library/golang@sha256:0056b049979bfcf13ac2ede60b810349396fab1d510cb60701503dccd01f9153" | |
| }, | |
| "annotations": null | |
| } | |
| ] | |
| }, | |
| "metadata": { | |
| "buildStartedOn": "2021-09-24T17:21:54Z", | |
| "buildFinishedOn": "2021-09-24T17:26:08Z" | |
| }, | |
| "materials": [ | |
| { | |
| "uri": "https://github.com/GoogleContainerTools/distroless", | |
| "digest": { | |
| "revision": "6cdf24fcc47ec93f370ea591f7ff460641a1ac5c" | |
| } | |
| } | |
| ] | |
| } | |
| } |
This contains not only the commit the artifact was built from, but also the container image (and digests) and arguments used for every build step in the process. These images themselves can be signed and have provenance, all the way back down to SCRATCH.
Wrapping Up
Aeva Black summarized the concept very well during my talk:
Applying these concepts to supply chains and build systems allows organizations to verify trust at every link in the chain. Perimeters don’t work for networks, and they don’t work for supply chains either.
Sigstore’s global transparency log allows us to get started incrementally by enabling anyone to publish metadata and attestations to a location that can be discovered by downstream users. As this graph fills out with more projects writing data as they build and release, we can strengthen the overall open source ecosystem. These same concepts apply internally to organizations, with concepts like innersource helping companies share code across teams and business units.
Combining these attestations with tightly integrated policy systems is the next step in automating compliance and tamper-resistance. If you’re interested in helping out, hop into the Sigstore slack or reach out on Twitter!
And if you’re interested in learning more about supply chain security register for SupplyChainSecurityCon happening on October 11 in co-location with KubeCon.


 by
by 
 , spooky
, spooky  (@aevavoom)
(@aevavoom) 



